Note: The content provided here is an updated, abridged and modified version of a weblog post titled, , that dealt mainly with the use of room controllers.
My preferred term for this subject area is not smart home, but domotics. Yet, not everyone appreciates Latin terms, when perfectly good Anglo-Saxon ones exist.
Part of the reason for my dislike of the term, smart home is the ascription of smart to basic electronic devices that are dependent on sensors and logical circuits, to actuate motors, lights and heaters. Another part of the reason is the use of home. For many people, this is an emotionally loaded term for a residence. I suspect some public relations/ advertising agency imagined that substituting home for residence, house or building would result in increased profits. Admittedly, there are other, more obnoxious phrases than smart home, such as the internet of things, a phrase I increasingly avoid.
Various dictionaries show the noun domus refers to house, home, family, household (with dependents), school (of philosophy). The adjective, domestic, is in common use in a variety of contexts. As a noun, it can refer to a hired household servant. Hopefully, in the future it will refer to a robot offering similar services, although dombot could emerge. If it does, expect puns contrasting dombot with dumbot.
MQTT Broker and clients
At the heart of any domotic device is communication. Andy Stanford-Clark and Arlon Nipper authored the first version of the Message Queuing Telemetry Transport (MQTT) protocol in 1999. The name is a misnomer, as there are no queues with MQTT. Typically, there are numerous clients, and at least one (and potentially more) message brokers. A broker receives all messages published by clients and then routes these messages to subscriber clients. In a household, a client is usually a micro controller, perhaps a Raspberry Pi, while the broker is typically software located on a Network Attached Storage (NAS) server.
In a home automation situation, publisher clients are attached to sensors, and they publish sensor data; subscriber clients are attached to actuators, typically motors, but also heaters, vents lights and much more, that they regulate, at the most basic level – turn on or off.
The two most common open source home automation systems using MQTT are: open Home Automation Bus (openHAB), a project started in 2010, with code written in Java; and, Homa Assistant, started in 2013, with code in Python. While Home Assistant has been praised for its privacy features, it has been criticized for its file-based setup procedure. Recently, it has become more user friendly and accessible, with a simplified, web-based graphical user interface. An iPhone or Android hand-held device, can also be used as controller. This is especially important when one wants to control features remotely.
Brokers and clients manage: lighting, temperature and humidity (indoor climate), audio and video (entertainment), unauthorized access, smoke/ fire detection (security) and related services. Here, it is only considered in terms of a residence, but almost all types of buildings can use these: barns, shops, manufacturing facilties, etc. While it might appear that micro-controllers are in charge, managing these services using algorithms, most systems can have their decisions overridden by humans.
Ethernet
Wireless communication, using Bluetooth or WiFi, should be avoided, if possible, for most domotic/ smart home automation hardware, because there will always be throughput and power issues with these technologies. The one exception to this rule is the use of hand-held devices, including mobile phones and tablets, that use apps to function as remote controls for the system. These apps can be downloaded from the appropriate device app provider.
In the previous millennium, it was not uncommon for people to wire their houses with Ethernet cable. People who did so, and have not removed them, are the real winners. The reason for this is that room controllers need to communicate, and to communicate they need power.
The various Ethernet cables were standardized for different speeds. Cat 3 provided 10 Mbit/s in a standard presented in 1990. Cat 5 increased throughput to 100 Mbit/s in 1995, and then to 1 Gbit/s in 1999. Cat 5e offered 2.5 Gbit/s in 2016, while Cat 6 increased it to 5 Gbit/s, the same year. The Cat6A standard, is actually ten years older, dating from 2006, but provides 10Gbit/s.
The advantage of Power over Ethernet (PoE) is that it eliminates the need to install separate power cables. PoE technology sends the above mentioned 10/100/1000 Mbps of data and 15W, 30W, 60W, and up to 90W of power to devices over Cat5e, Cat6 and Cat6A Ethernet cables for a maximum distance of 100m. Cat3 and Cat5 cable can also be used with restrictions, They supply of 48 V with a maximum current of 400 mA using two of the available four pairs of wires on Cat 3 or Cat 5 cable. While this appears to provide a maximum power of 19.2 W, system losses will normally reduce this to under 13 W.
MQTT Software and supporting hardware
The household’s MQTT broker is typically a software program, housed in a server. Wifi-based handheld devices connect to the broker using Wifi, while Ethernet-based room controllers connect to it through cables, and a switch.
A switch is a box that allows multiple other devices in a local area network to be inter-connected. A typical commercial switch may have up to 48 different ports for cables connected to 48 separate devices. Home oriented switches typically have 8 ports.
Business users commonly sell off their equipment once the warranty period has expired. Servers as well as switches can be purchased by private individuals inexpensively, because businesses won’t buy used (read: out of warranty) equipment, and most people don’t know what the equipment can be used for.
Cables usually run between the switch and other devices through the walls of the house, although there is nothing to prevent more visible wiring, along walls/ ceilings/ floors. If people are considering remodelling their house, adding Ethernet cable is no real issue. Whatever cable is used, it will ultimately pay to use the fastest Ethernet cable type currently available that supports PoE. Cat 6 is more readily available than Cat 6A. Using either means that the cable won’t have to be replaced anytime soon. Hopefully, the cables will last 30 years, or more.
Room Controllers
Control units, like all devices, needs power. Power over Ethernet (PoE) is an ideal way to provide power, since Ethernet connectivity is the preferred approach to wired data communication. PoE eliminates the need to install separate power cables. Each controller is provided with power from the switch itself.
Several different types of microprocessors can be used in controllers, including Arduino, ESP and Raspberry Pi. At Cliff Cotttage, Raspberry Pis are used.
Room controllers, and similar devices, are one of the main categories of devices that need PoE connections. A typical unit could use a Raspberry Pi Model B 3+, sensors connected to general purpose input-output (GPIO) pins. with a PoE hat (hardware on top, which provides extra capabilities) to provide power and cooling, and – in addition – a Pimoroni Automation HAT to provide support for actuators. Some room controllers would have a 7″ touch screen. Others would be fitted for voice communication with microphones and speakers.
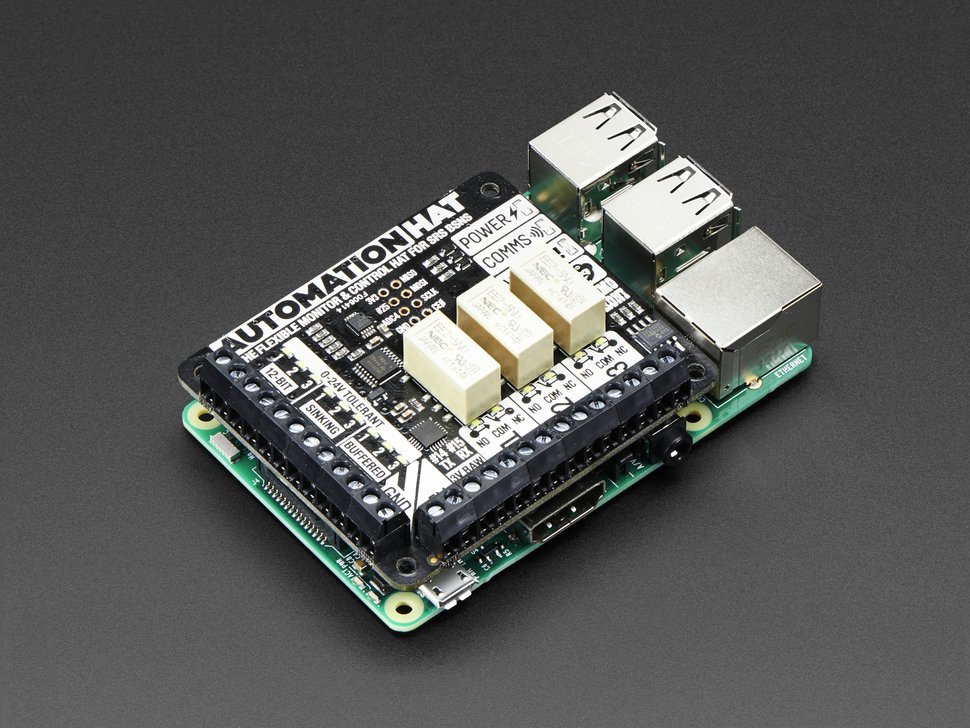
Controllers need to be placed in the following locations: 1) access control at entrance doors; 2) living room; 3) dining area; 4) kitchen; 5) bedrooms; 6) study, studio and workshop areas. A few people may want to have controllers in 7) bathrooms and/or laundry rooms, while most prefer to avoid this. In addition, there shouldl be 8) PoE access points for WiFi. This allows WiFi connections in parts of the house that are inaccessible for direct signals to and from the server.
Other switches, without PoE, can be used for other devices dependent on higher power levels. These include: 1) a home theatre connections; 2) a printer and/ or scanner; 3) clothes washer and/ or dryer; 4) dishwasher; 5) refrigerator and/ or freezer; 6) stove top and/ or oven; 7) microwave oven; 8) kettle; 9) hot water tank; 10) heat exchanger; 11) heat pump or solar thermal controller; 12) greenhouse controller. Not everyone has appliances with Ethernet connections, but they are increasingly available.
A front-door access controller will typically have an infra-red camera, proximity sensor and infra-red light connected to it, that will be activated as someone approaches. Video of each event will be sent to an external location, that could be located anywhere in the world. A room controller may have proximity sensors as well as other sensors to register temperature, CO2, humidity levels and more. Data gained from these sensors and others throughout a house, can be used to activate lights, or heating, display time, temperature and other data on a touch screen. It can even listen to verbal instructions with a microphone and answer using a speaker.
Recently, a Compute Module (CM) 4 was released. Unlike more conventional Raspberry Pis, the CM is totally flat, but uses the bottom edge for connection. In the future, I hope to acquire a Compute Module 4 Development Kit to develop suitable applications based on these modules. CM boards are used because they avoid unnecessary components, making products potentially cheaper and smaller.
Update of content in Printers, published 2020-03-24:
Owners of H-P and other ink jet printers, are advised to read what Cory Doctorow has to say in Ink-Stained Wretches: The Battle for the Soul of Digital Freedom Taking Place Inside Your Printer (2020-11-05).