Even weblogs must have ethical standards.
Jim Lehrer (1934 – 2020) constructed a list of 16 Rules of Journalism, printed in italics at the beginning of the paragraphs below. These were later reduced to nine rules, marked with an *. These rules were copied from Kottke, who comments on them in general, and points to their original sources. I am using them as a starting point for my own personal reflections on weblogging. It does not mean that I favour these rules over other rules, for many have infuriated me. Others, not so much. Some rules have not been commented upon. Others have. See, especially, rule #15.
- Do nothing I cannot defend.* Coming first and with an *, it could be an important rule, but it grates. It is defeatist, starting with the negative (do nothing) rather than the positive (so something). Even the term defend points in two directions. Is Lehrer concerned about protecting something? or is it about showing support? My replacement would be: Promote causes that you endorse. Cause could refer to a principle, ideal, goal or movement to which a person is dedicated, or the end/ purpose for which a thing is produced, or even something broader still, such as the general welfare of the planet/ humanity/ a more restricted group/ person. Endorse includes a range of support (middle ground), from approval (weaker), to sustain or defend (stronger).
- Do not distort, lie, slant, or hype. This is a difficult rule to follow, especially the slanting. A slant is a perspective on a problem. All events have to be viewed from some perspective, even if they aren’t acknowledged. Where does slanting stop, and hype and/or distortion begin? How much distortion, hype or slanting does it take, before the result is considered a lie? There are no easy answers. One reason for weblogging is to present alternative opinions, especially those that are not supportive of the mainstream, which for me consist of a libertarian perspective on the economy, and a conservative perspective on social life, that are found/ distorted/ lied about/ slanted/ hyped in commercial media.
- Do not falsify facts or make up quotes. Quotations and other attributions of thought are difficult. In part, it comes from the inability of some people to speak/ write succinctly enough. Often, there is a need to re-state the essence of a person’s opinion, without distortion. At another level it also reveals a major challenge with journalism and its focus on individuals, rather than systems. One criticism of journalists is that some seem more interested in a subject’s passion or conviction, rather than the truth of their statements.
- Cover, write, and present every story with the care I would want if the story were about me.* Washington Post reporter Felicia Sonmez (1983 – ) tweeted a link to an article about the 2003 rape accusation against Kobe Bryant (1978 – 2020), who died on 2020-01-26 in a helicopter accident. Sonmez was subsequently harangued and threatened, her address posted publicly, and her employer placed her on administrative leave. Bryant issued an apology where he made clear he believed the woman when she said she did not feel their encounter was consensual. The Median article describing the Sonmez situation, reasons that that public relations were more important to the Washington Post than Sonmez herself. It wonders why rape victims would trust the Washington Post with their stories if they think the paper is more concerned with appeasing an online mob than holding powerful men to account? It concludes that a powerful publication silenced its female reporter for tweeting about rape. Lehrer’s rule seems to suggest he would prefer people not to write about rape, or any other uncomfortable subject, at least when the alleged perpetrator is a celebrity.
- Assume there is at least one other side or version to every story.* One of the reasons I have stopped reading a particular local newspaper, is that – from my perspective – it covers stories by focusing on one single person/ perspective, and allowing that one person to frame events. There seems to be no balance, until later – perhaps – when a second perspective is described, that is 180 degrees away from the first. Even then, it is difficult for the second party to address issues, because they have already been framed, possibly detrimentally.
- Assume the viewer is as smart and caring and good a person as I am.* Radio, television, newspapers (and more) are mass media, sending out their stories to thousands, if not millions of listeners, viewers and/ or readers. The audience of this weblog is entirely different. It currently consists of 32 other people. Each of these people I know personally, even if there are some that I have never met in person. Others, I may not have met for over fifty years. I have also stated that if this weblog has an audience of more than 100 people, I will have failed at my goal. I have no desire to be famous, or to be popular. Perhaps Bernie Sanders (1941 – ) has expressed it best. Responding to a comment by Hillary Rodham Clinton ( 1947 – ) that no one likes him, Sanders replied, “On a good day, my wife likes me.” This weblog is not trying to influence anyone, apart from a very select group who are (hopefully) equally smart, caring and as good as I am. It is encouraging people to forget mass-market social media, and to engage with a limited number of real friends on issues that are of importance to that small group of people.
- Assume the same about all people on whom I report.* I presume this rule is actually stating, that journalists must assume that the subject of a story is as smart and caring and good a person as the journalist reporting. This makes an assumption that stories are about people. Many of my stories are about technology, sometimes its failings, at other times it successes.
- Assume everyone is innocent until proven guilty. In its editorial on 2020-01-24, Logisk brist = Logical Deficiency, the Inderøyning newspaper takes up the legal situation of a Norwegian woman and her two children, who have been returned to Norway from Syria. The problem is that leading politicians have pronounced the woman guilty of terrorism, despite the lack of any legal judgement against her, in violation of the Norwegian constitution. Her return to Norway has even led to the Progressive Party, leaving the government. In social media, including weblogs, it is far too easy to defame people who must be presumed innocent. It is my understanding that no court of law has found this woman guilty of anything.
- Assume personal lives are a private matter until a legitimate turn in the story mandates otherwise.* When I initially read this statement, my mind turned to social media, and how it is encouraging precisely the opposite of this rule. For even the most intimate details of a person’s life are exposed and commented upon.
- Carefully separate opinion and analysis from straight news stories and clearly label them as such.* This rule shows by example, the challenge of finding suitable rules. I think I understand all of the words in the rule until I get to the phrase straight news stories. It grates. Even if journalists use the term story, it is too close to the concept of fiction for my liking. I suspect a news story is a spicier version of a sequence of news facts. Since the adjective straight is being used to modify news story, I am left wondering what other varieties can be found. When I look up straight in a dictionary I find 19 different meanings, including not curved and heterosexual. Fortunately, it also provides me with a better understanding of its journalistic meaning: written or to be written in a direct and objective manner, with no attempt at individual styling, comment, etc. If I were to help Lehrer, by re-writing the rule for him, it would be: Separate and label facts, opinions and analyses.
- Do not use anonymous sources or blind quotes except on rare and monumental occasions. No one should ever be allowed to attack another anonymously.* While sources are sometimes lacking in this weblog, when people are mentioned, I try to put in their name as well as their year of birth and death, to try to put that person’s experiences into context. The same is also true, with respect to the first publication date of a book or article. Unfortunately, not all C.V.s contain essential information, such as year of birth. There are times when I feel I should go further, and include country of birth, or at least residence. L. P. Hartley (1895 – 1972) wrote in The Go-Between (1953), “The past is a foreign country; they do things differently there.” It is often difficult to understand what has motivated people. Even more difficult if the context of their life is missing. Personally, I am a pacifist, and refuse to use weapons. Yet, both of my parents, Edgar (1906 – 1991) and Jennie (1916 – ) served in the Royal Canadian Air Force during the second World War. While I have been able to condemn almost all wars since then, I still have difficulties understanding WW II, and passing judgement on its participants.
- Do not broadcast profanity or the end result of violence unless it is an integral and necessary part of the story and/or crucial to understanding the story.
- Acknowledge that objectivity may be impossible but fairness never is.
- Journalists who are reckless with facts and reputations should be disciplined by their employers. This is a very naive statement, given that much of the media is owned by entrepreneurs wanting to promote a particular political perspective. The right-leaning (Kieth) Rupert Murdoch (1931 – ) through his News Corporation, owned over 800 companies in more than 50 countries, with a net worth of over $5 billion in 2 000. In other ages, there have been other media moguls with other priorities. William Randolph Hurst (1863 – 1951) favoured the working class, who bought his papers, and denouncing the rich and powerful. Today, Mark Elliott Zuckerberg (1984 – ) has become infamous for Facebook’s role in allowing Cambridge Analytica to harvest personal data from millions of Facebook profiles without their consent and using it for political advertising purposes.
- My viewers have a right to know what principles guide my work and the process I use in their practice. Change viewers to readers, and the statement should be true of every serious weblog. Thus, I am curious to know what readers believe should be the principles followed in this weblog. Readers with opinions are encouraged to comment. Those reluctant to do so publicly, are encouraged to send a confidential email. While I will read and evaluate all material sent, this does not mean that I will incorporate it in any final rules for Brock’s weblog.
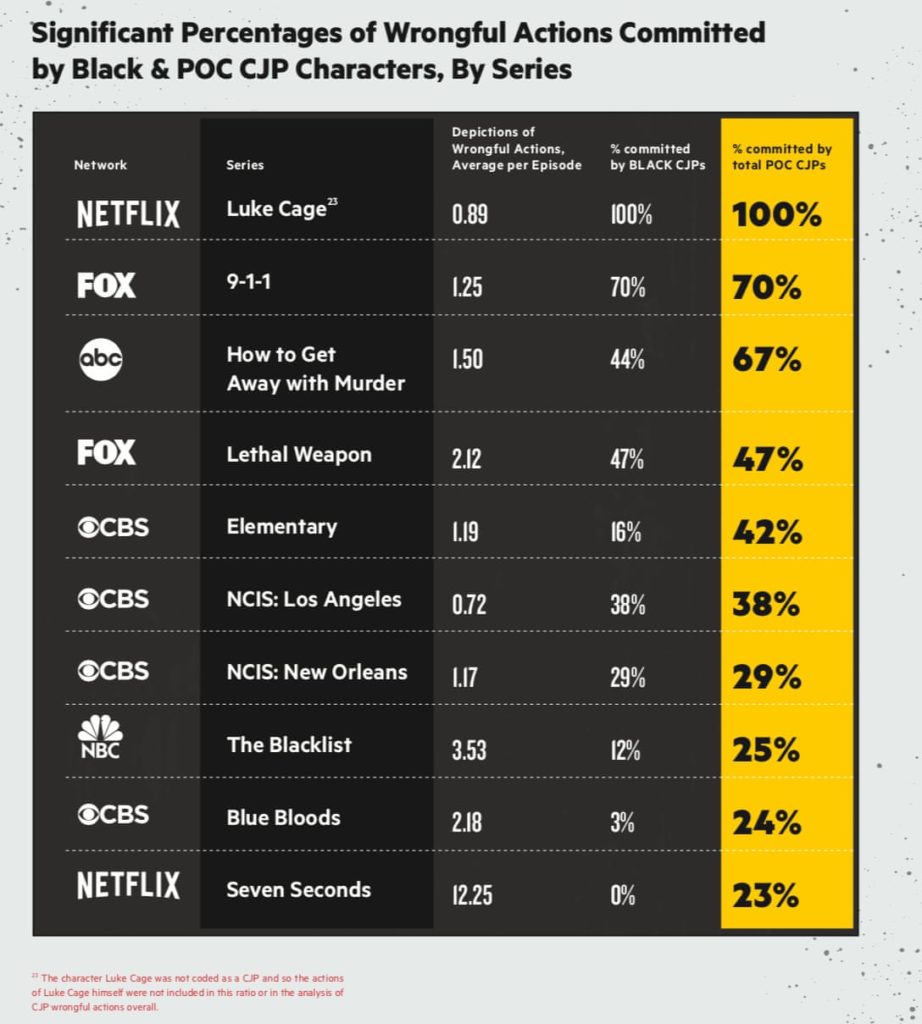
- I am not in the entertainment business.* That is a debatable point. Everything related to the media can be considered entertainment, even if some regard themselves above it. Much of the harm initially done there, is subsequently amplified by webblog posts. Take television crime drama, as an example. In Change of Color’s report, Normalizing Injustice, a disproportionate number of wrongdoing criminal justice professionals are black or people of colour, as shown in the table at the beginning of this weblog post. This report reminds people that “the crime genre glorifies, justifies and normalizes the systematic violence and injustice meted out by police, making heroes out of police and prosecutors who engage in abuse, particularly against people of color.” Misconduct is often presented in a way that normalizes it, making problematic characters seem good and their wrongful actions justified. Fiction is not just fiction, and entertainment is not simply entertainment, both are tools that shape attitudes. Entertainment cannot be ignored, for it can be the face of oppression.
This marks the end of Lehrer’s rules. What do readers think should be in a set of rules that should apply to all weblogs? In addition to these, what other rules should apply specifically to Brock’s weblogs?